In August 2023, Workspace ONE UEM extended conditional access capabilities for Microsoft Entra ID (formerly Microsoft Azure Active Directory) with…
How to deploy macOS PaperCut using Workspace ONE
PaperCut is used by businesses and organizations to track, control, and optimize their printing. PaperCut MF allows businesses to set…
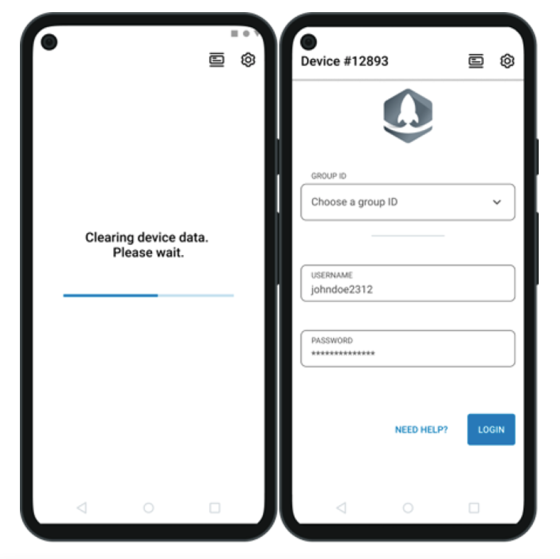
Setting up Workspace ONE Android Check-In Check-Out (CICO) with Okta or Entra ID (Azure AD)
Workspace ONE Launcher lets IT administrators design a custom home screen for Android devices. You can easily layout your applications…
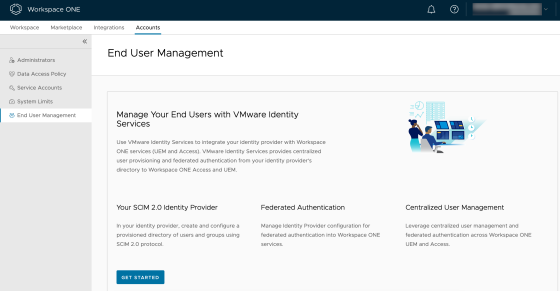
Integrating VMware Identity Services with Okta
VMware Identity Services is a relatively new service that allows organizations to centrally manage their cloud-based identities in Workspace ONE…
Getting Started with VMware Digital Employee Experience (DEX)
VMware Digital Employee Experience (DEX) measures workplace experience, analyzes data, helps deliver a high-level employee experience, and helps remediate issues…
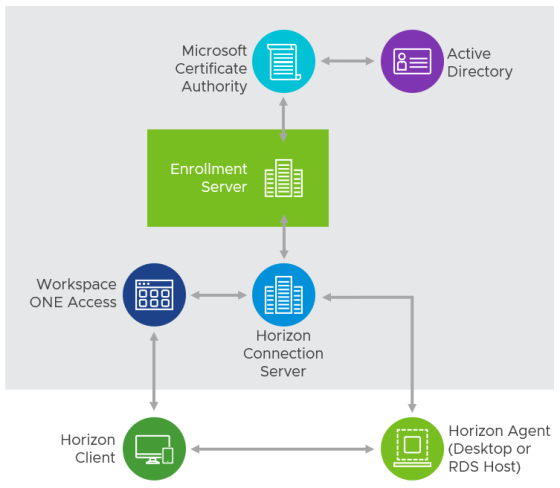
Enabling and Troubleshooting VMware Horizon True SSO
True SSO was introduced by VMware Horizon back in 2016. It allows users to authenticate with Workspace ONE Access using…
Configure Okta as an Identity Provider for VMware Workspace ONE Access
This blog article describes how to configure Okta as the identity provider to Workspace ONE Access. You can use this configuration…
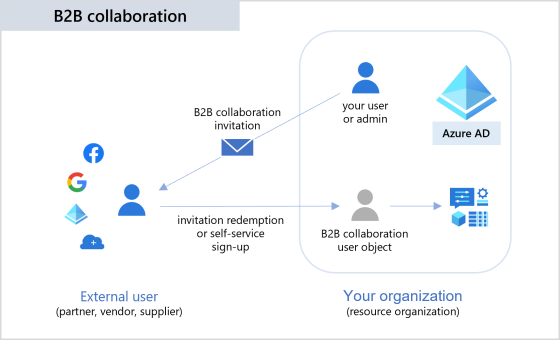
Streamline 3rd party application access with VMware Horizon by leveraging Azure AD B2B Guest Accounts
Most organisations need to provide secure access to third party organisations to their on-premises applications. How can you achieve this…
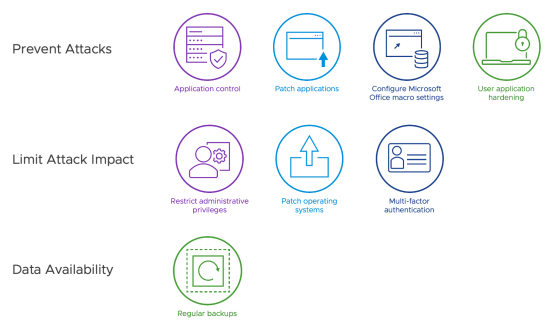
Implementing the ACSC Essential Eight with Workspace ONE UEM and Intelligence
The Australian Cyber Security Centre (ACSC) Essential Eight Maturity Model provides a set of recommended cyber principles for organisations of…
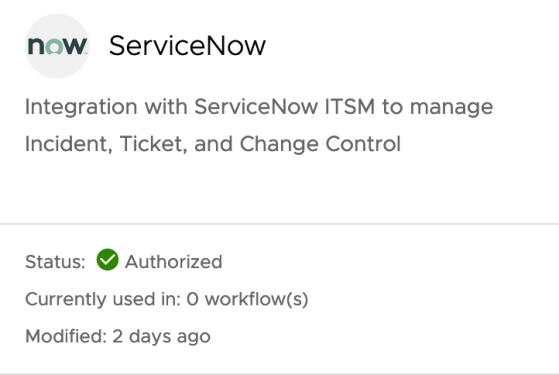
Integrating Workspace ONE Intelligence and ServiceNow
Workspace ONE Intelligence provides a number of out of the box integrations with solutions such as ServiceNow. This allows administrators…